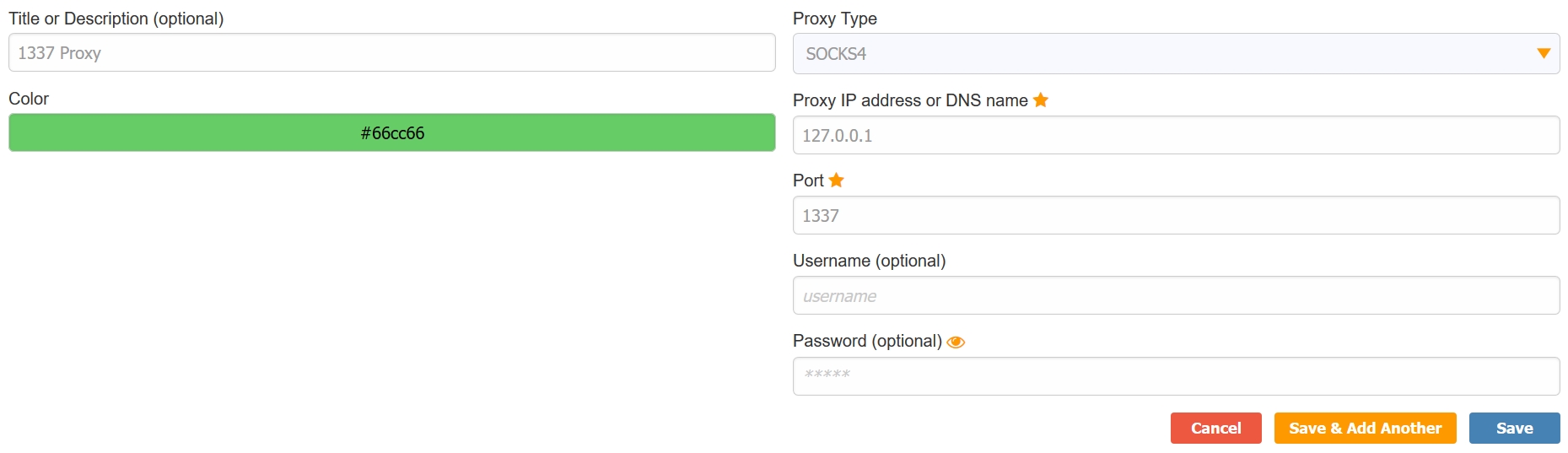
Tunneling
Proxychains
Comment the proxy_dns line in the /etc/proxychains4.conf file
Create a Forward Proxy by connecting to machine via SSH and port forward default Proxychains port
ssh -f -N -D 9050 [email protected]
-f backgrounds ssh
-N doesnt execute remote commands
-D bind with port 9050Use Proxychains with commands
proxychains nmap -sC -sV -T4 10.10.200.0/24proxychains xfreerdp /u:administrator /p:'Password1' /v:10.10.200.225SSH Tunneling
There are two ways to create a SSH tunnel using the SSH client which are port forwarding, and creating a forward proxy
SSH Port Forwarding
Create a link to an internal webserver (172.16.0.10:80) using port 8000 and SSH access to the compromised machine (172.16.0.5).
-L creates a link to the Local Port
-f backgrounds the shell
-N no commands to be executed
You have SSH access to a server (172.16.0.50) with a webserver running internally on port 80 (i.e. only accessible to the server itself on 127.0.0.1:80). Forward it to port 8000 on your machine
Reverse SSH Connection (ABSOLUTE NO NO)
Anyways..
Very risky but ideal if you have a shell on the compromised server but no SSH access.
Generate a new key pair
Copy the contents of the public key (the file ending with .pub), then edit the ~/.ssh/authorized_keys file on your ownmachine. You may need to create the ~/.ssh directory and authorized_keys file first.
Paste this line on a new line in the public key
Start the SSH server
Transfer the private key and connect back to your machine
Should mainly be used for any internal webapps