Findings Report
Overview
A Findings Report entails everything that you did and found on a high and low level. This section will have very quick and short notes on each section of the Findings Report, highlighting the importance of each one and what they're about
TCM Security Sample Report
Disclaimer
A Disclaimer saying that the test is a snapshot in time meaning that after the week of engagement if someone opens up a port or puts up an new vulnerable application, we are not responsible for that.
The engagement is time limited meaning that we can only target what we can in that period of time. When limited on time not going to find everything)
Some clients will be cheap and pay for a week instead of two not giving a good in depth engagement
Assessment Overview
High level overview
State that all testing is performed based on the NIST XXXXX
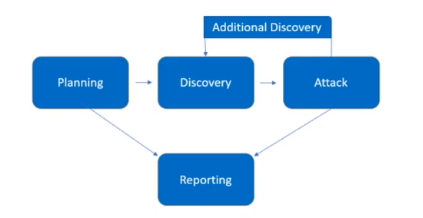
Show the phases of the pentest life cycle
Assessment Components
State what an external penetration test is (or whatever kind of pentest you're doing)
Multiple components = multiple statements
Findings Severity Summary
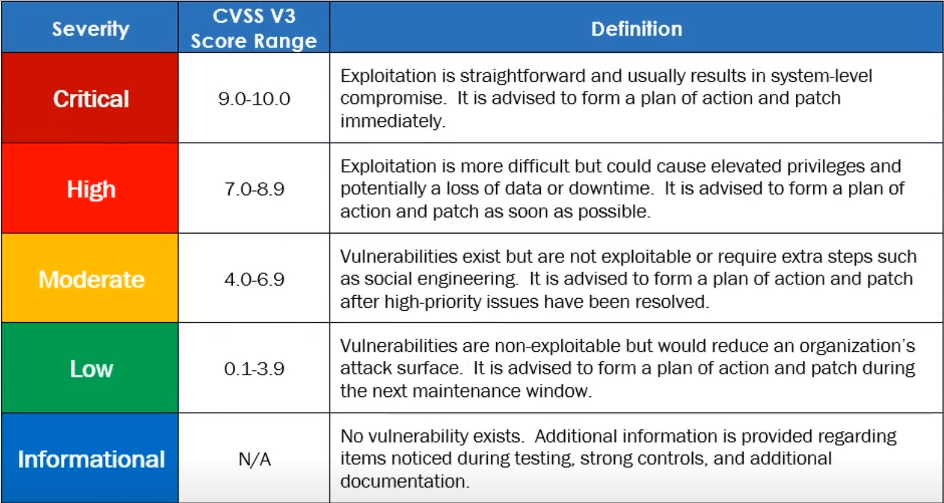
Must rate findings based off severity
Use the CVSS V3 score rating chart
The severity rating is based off of Likelihood and Impact which can be subjective
Example: You find a XSS vulnerability in one of their web applications but they had it accessible through a whitelist only. This would make the Likelihood of the attack go down along with the severity rating (High or Moderate).
Scope
Each assessment will be paired with details stating which IP addresses are in scope
Scope exclusions will be stated, usually DoS and Social Engineering
Client allowances ; did the client assist you in any way?
Provide a password or access to an account
Executive Summary
This summary is for someone who is a C Level Executive
They probably won't come from a technical background so dumbing down the concepts is important
Scoping and Time Limitations
State what the timeline and scope were
Testing Summary:
This is a quick summary of what attacks were preformed and what they findings were
Don't get into too much of the technical details (tools, crazy techniques, etc.)
Include what was compromised and what you could see
Should only be High or Critical findings
Security Strengths
Provide summary of what their strengths were (SIEM alerts/prevention, firewall alerts, etc.)
Security Weaknesses
Summary of where their securty holes are (MFA, Weak password policies, Unrestricted logon attempts, etc)
Vulnerabilities by impact
Add a pretty chart with the severity rating scores
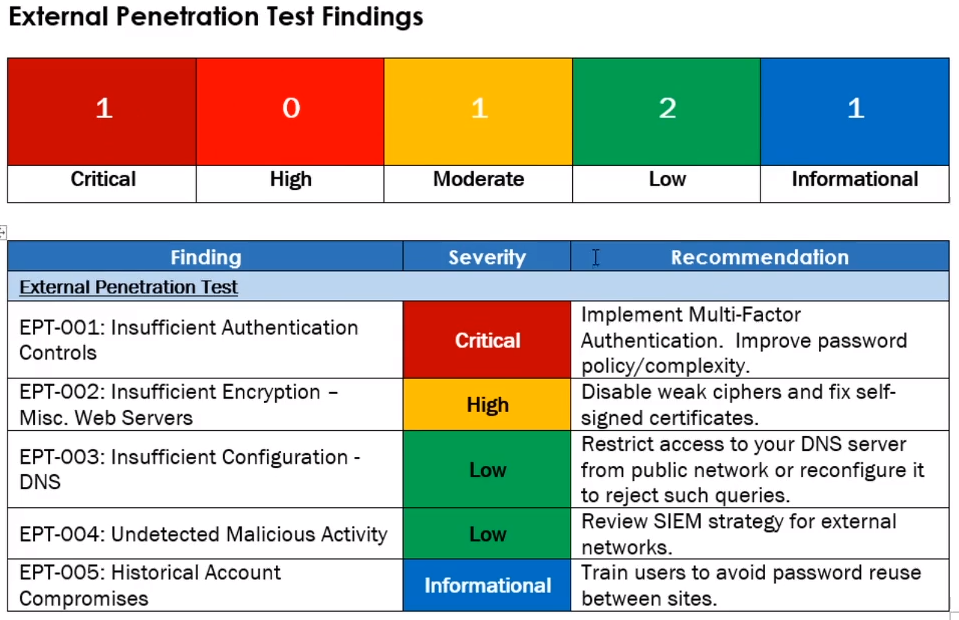
Pretty chart example
Technical Findings
Technical summary for the more technical people (network engineers, security analysts etc.)
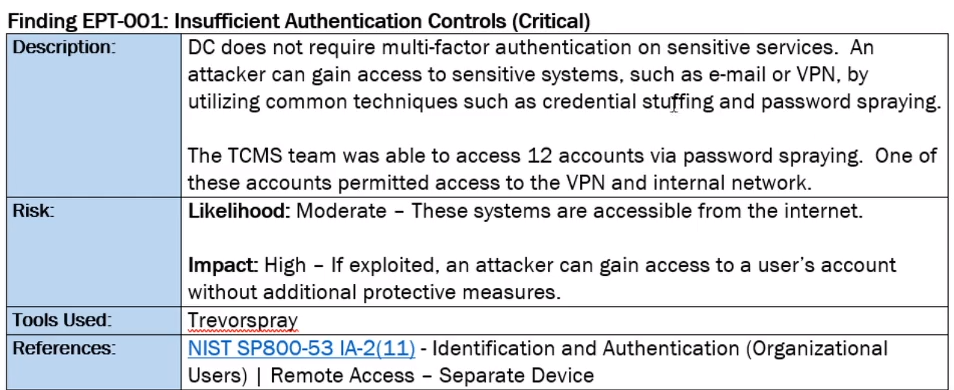
Each finding will be it's own section ranked from most Critical to Least Critical
Includes Description, impact, system(IP), references (NIST doc) and a PoC
Have pictures to help explain everything as well
Don't have a picture for everything so it's step by step. That can be too much
Next should be a Remediation section for that finding
Who should fix it?
Attack vector (remote, internal etc.)
Actions that should be taken to remediate
Informational Findings
This can include credentials from breached dumps
Blur out passwords on the report but leave the Users visible
Additional reports and scans
Provide all of the outputs (Nmap scans summary, Nmap scan by host, Nessus scans)
Use excel or PDF documents
It's important to include scans because if there's a lot of critical/high vulnerabilities and a few medium ones, the report will only have critical and high but there's more things going on in the scans a lot of the times