Impersonation and Potato Attacks
Token Impersonation Overview
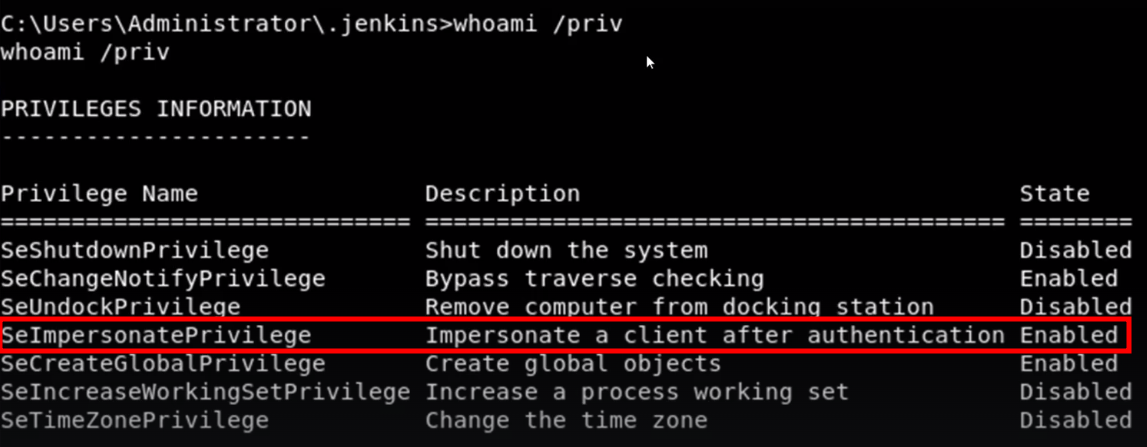
Potato Attack Overview
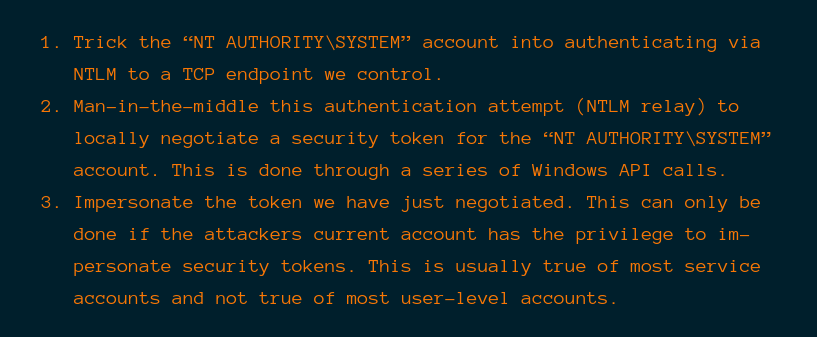
Escalation via Potato Attack
Manual Juicy Potato Attack
GOD POTATO
Resources
Bonus
Alternate Data Streams
Last updated
