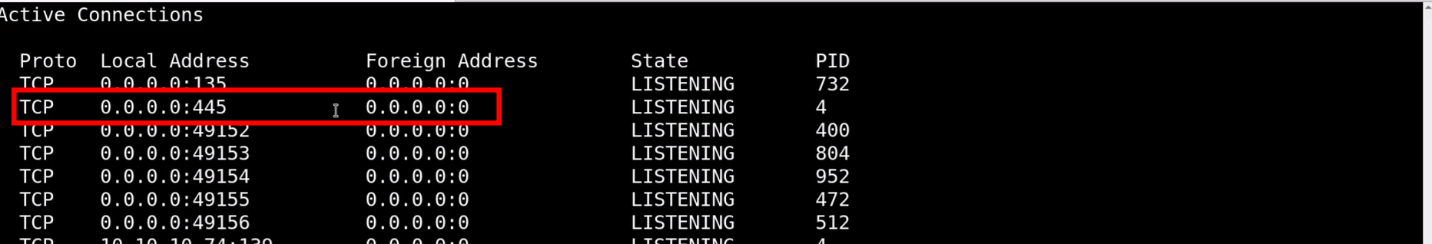
Stored Passwords and Port Forwarding
Overview
Registry Passwords
reg query HKLM /f password /t REG_SZ /s
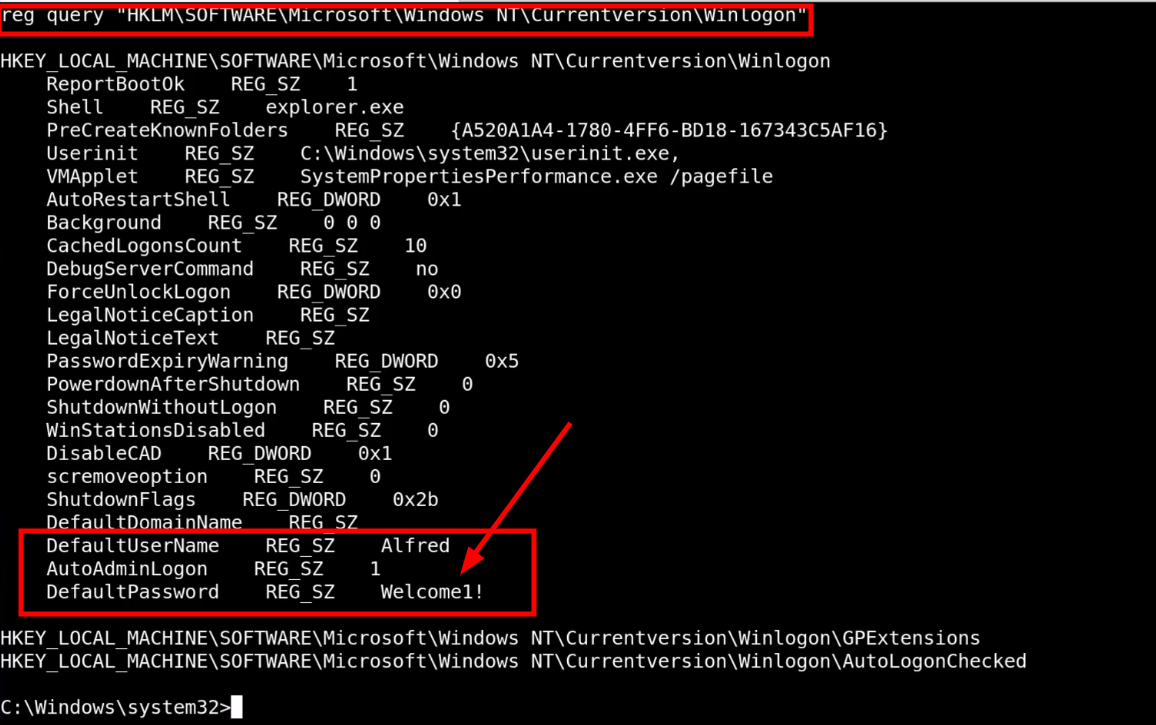
reg query HKCU /f password /t REG_SZ /sreg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"Example output
Port Forwarding