SUID
Overview
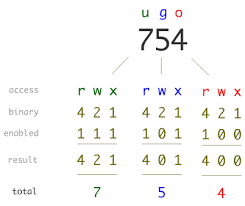
4 bits for READ, 2 bits for WRITE and 1 bit for EXECUTE. chmod 777 would be rwx across the board
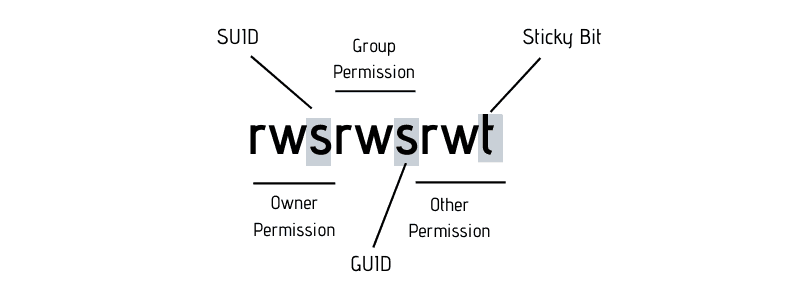
Files with SUID (Set User ID) permissions allows the file to ran with permissions of another specified user
Escalation via SUID
Note down any interesting binaries and run them to see what they do
The strace debugging tool can be used to monitor and trace/track what a binary does when its ran.
We want to find output that says "No such file or directory". We can then overwrite the file path/file with something malicious that will give us a root shell.

Check to see if the file path is writeable and create malicious .so file
Then run the original binary file
Escalation via Binary Symlinks
This has to do with a vulnerability Nginx and utilizing SUID to escalate to root.
Because of the way that the logs are being created by Nginx and how their permissions are set, we can leveraged this to go from a www-data user to root.
Manually find it with dpkg. Any version <= 1.6.2 is vulnerable
Next find out if there is a SUID bit on /usr/bin/sudo
Now we can create a Symlink between one of the Nginx log files and a malicious file so when it runs it runs as root
We need a startup/restart of the Nginx server for the malicious file to run
Run the nginxed-root.sh tool and wait for Nginx to restart
Escalation via Environmental Variables
Environmental variables are variables that are available system wide and are inherited spawned by all child processes and shells
Check what the environmental variables on the machine are
Find a binary with the SUID bit
Read the strings of binary files
While digging through the files you may come across the program trying to run another binary just by its name without using the full path. It can only do this because of the /usr/local/bin environment variable set in the shell.

We can exploit this by changing the env binary path of service and replacing it with a malicious service binary file
Spawn root shell binary file as a one liner
Compile
Change the $PATH variable and call the orginal binary
ALTERNATIVE
In the case that the binary is calling a full path a function with the name service can be made with that spawns a new shell
export the function ( the -f means refer to shell function)
Run the original binary
Last updated