Bloodhound
Overview
Bloodhound works the same way that ldapdomaindump but it also collects data using Kerberos tickets and SMB sessions.
Bloodhound allows for better visualization of attack paths, misconfigurations and potential privilege escalation paths.
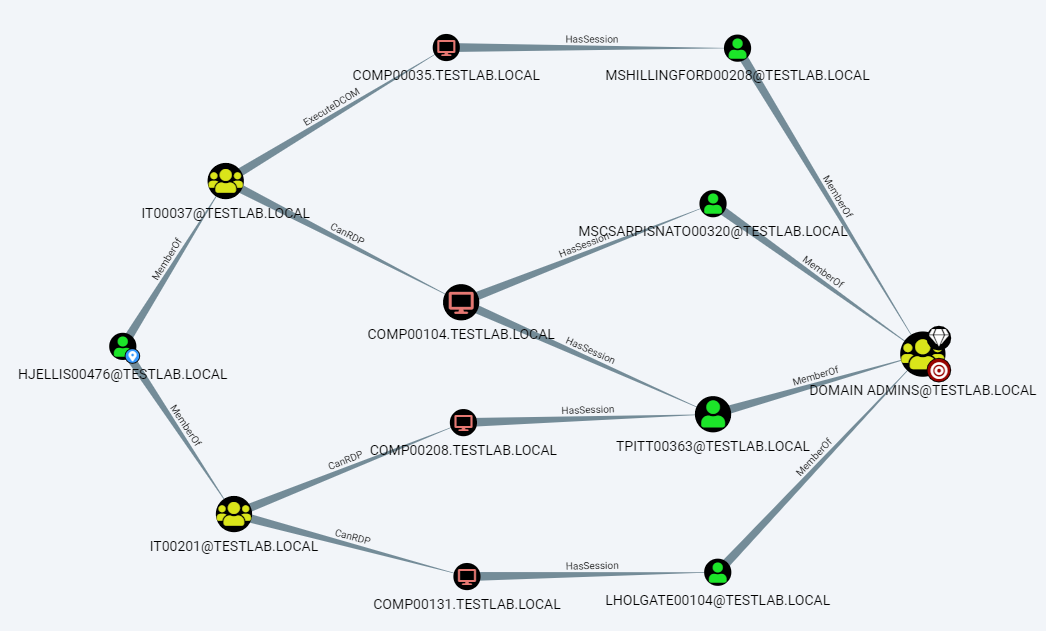
Domain Enumeration
Upload the dumped files into the Bloodhound GUI
Custom user to machine session query
Sharphound
If you don't have valid AD credentials and only an open shell you can run sharphound.exe to collect the data
This is very noisy so it should only be ran if you don't mind the noise
Methodology
Mark all pwned machines
Check Reachable High Value Targets
Essentially checks if that one machine could compromise the entire domain
Check Inbound Control Rights
What can account/gorups can control this object
Check Outbound Control Rights (First Degree Object Control)
What objects can our compromised machine control
DCSync/GetChangesAll
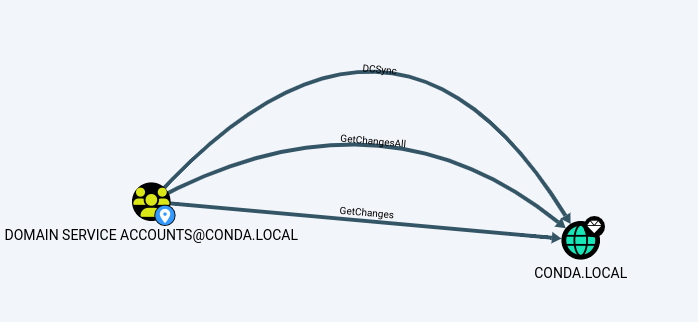
If you have GetChanges and GetChangesAll privileges you can perform a dcsync attack. This attack abuses dcsync and the way it works with syncing domain controllers together to make sure that they both have the most up to date data. This means that we can extract all of the NTLM hashes by requesting a dcsync with the domain controller.
Add yourself to the Domain service accounts
Amsi bypass then use mimikatz
Grab domain admin hash
Last updated